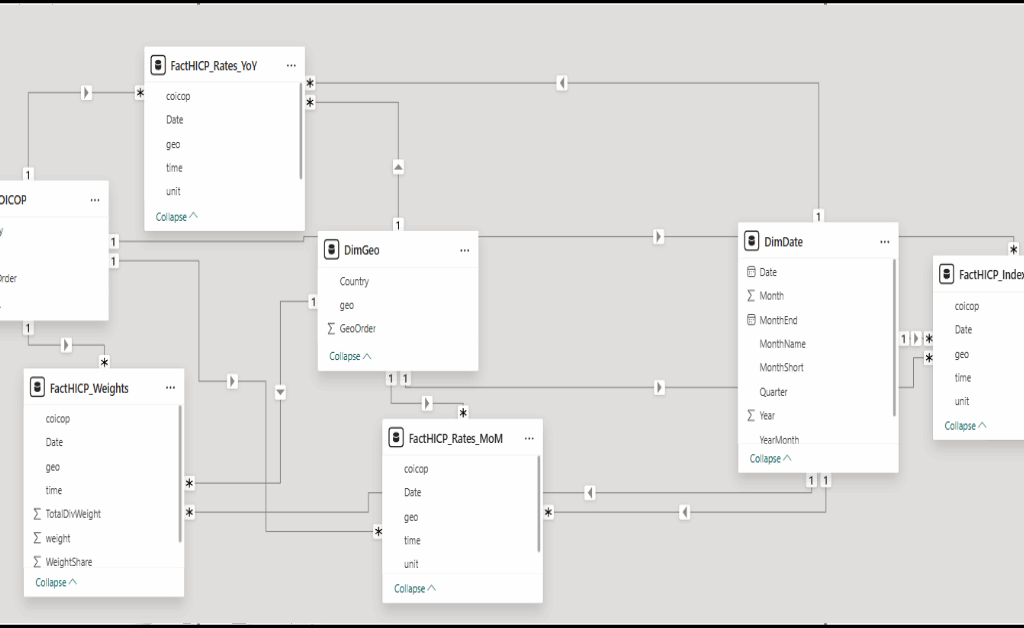
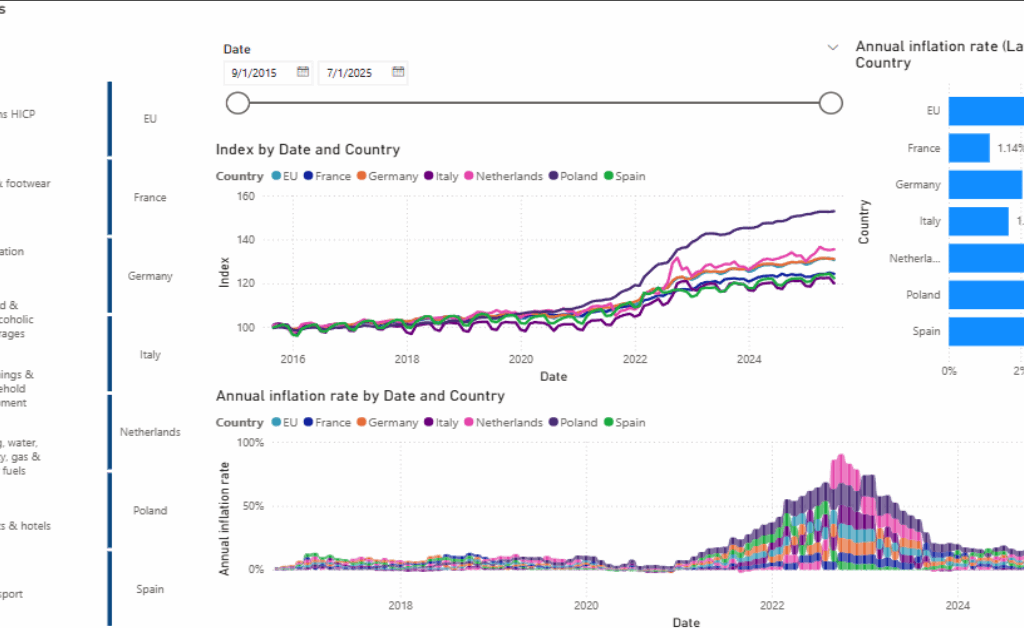
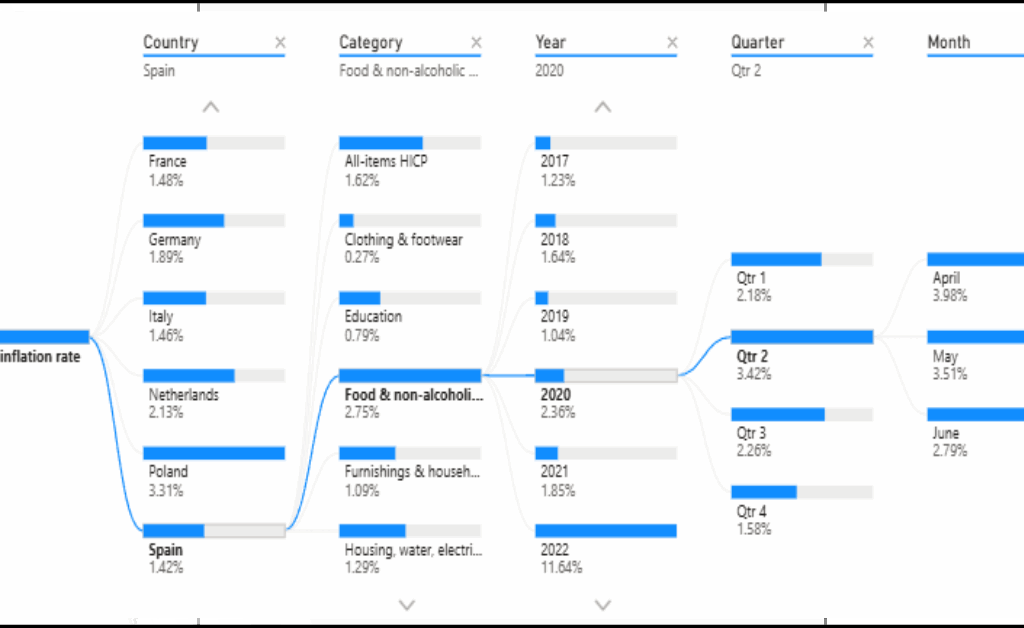
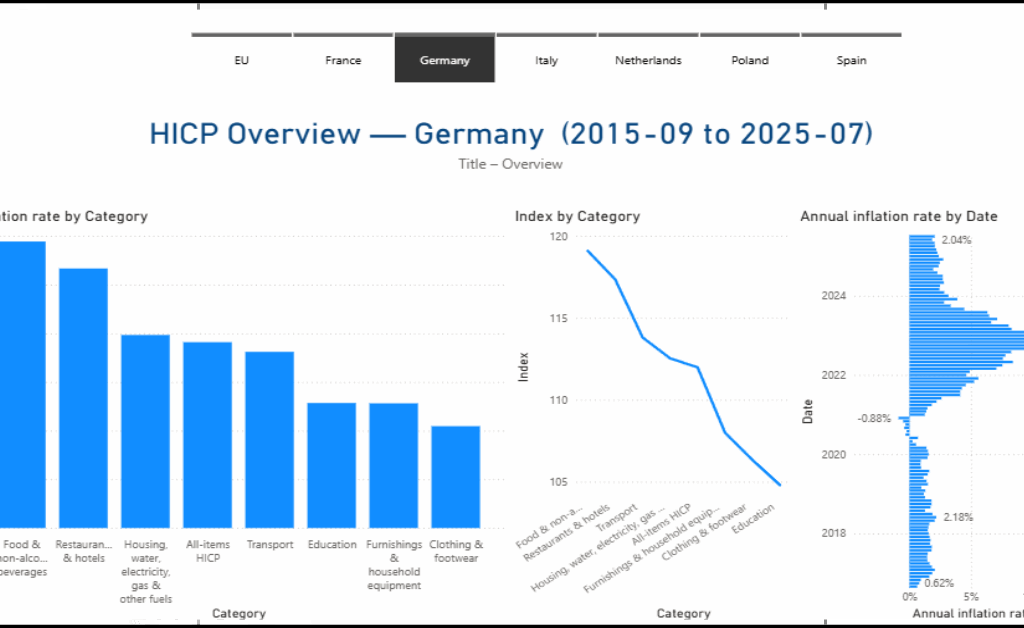
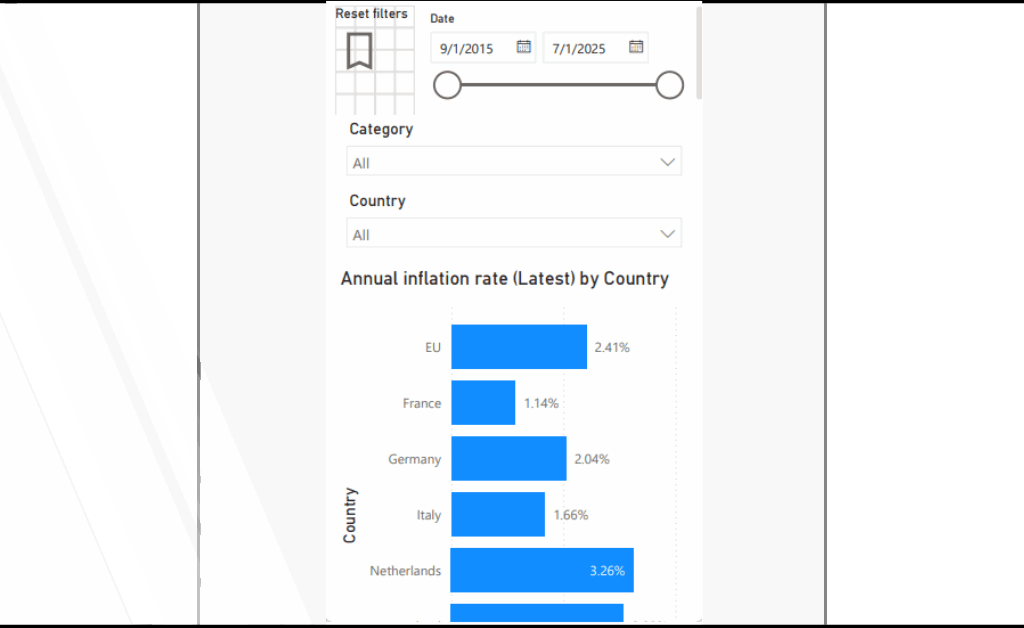
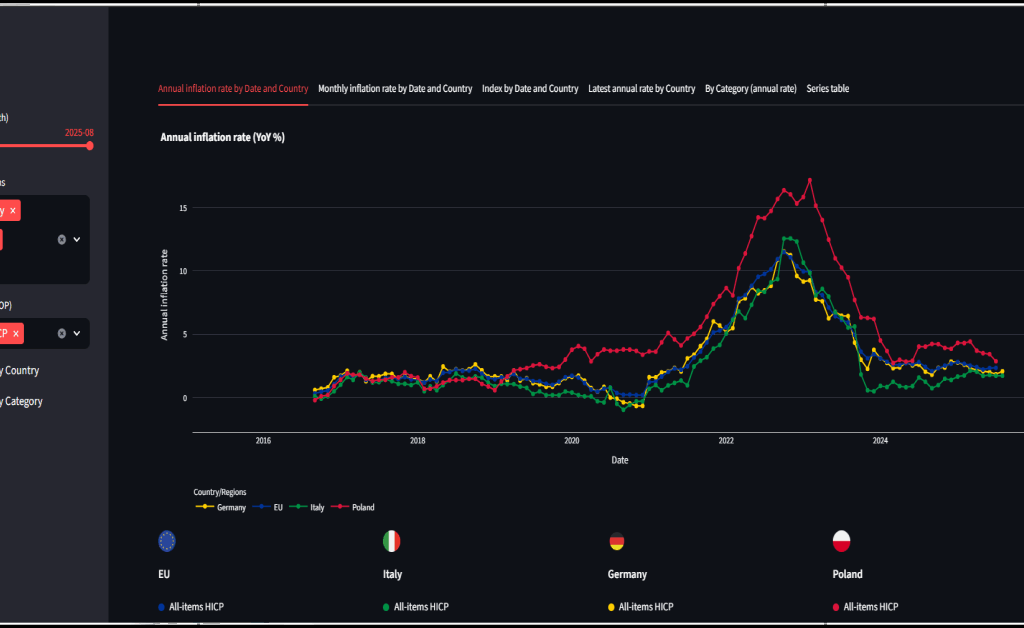
Dieser Artikel dokumentiert die Renovierung eines älteren Bestandsgebäudes aus der Perspektive der Planung, Umsetzung und fachlichen Entscheidungsfindung. Im Mittelpunkt steht Renovierung nicht als isolierte Baumaßnahme, sondern als ganzheitlicher Prozess, der den respektvollen Umgang mit bestehender Bausubstanz, die Verbesserung von Sicherheit und Energieeffizienz sowie die Anpassung an zeitgemäße Nutzungsanforderungen miteinander verbindet. Anhand eines realisierten Projekts wird gezeigt, wie architektonische Identität bewahrt, technische Systeme erneuert und räumliche Qualitäten weiterentwickelt werden können, ohne den historischen Charakter des Gebäudes zu verlieren. Der Beitrag versteht sich als praxisnaher Erfahrungsbericht und verdeutlicht, dass qualitätsvolle Renovierung einen nachhaltigen Beitrag zur langfristigen Nutzung und zum Erhalt urbaner Strukturen leisten kann.
Nazanin Farkhondeh, Cademix Institute of Technology, Austria
Renovierung als Haltung, nicht als Maßnahme
Renovierung ist kein rein technischer Vorgang. In meiner beruflichen Praxis habe ich Renovierung immer als eine Haltung verstanden – als bewusste Entscheidung, mit bestehender Bausubstanz verantwortungsvoll umzugehen, statt sie durch standardisierte Neubauprozesse zu ersetzen. Gerade bei älteren Gebäuden geht es nicht nur um Substanz, sondern um Erinnerung, Identität und städtebauliche Kontinuität.
Dieses Projekt steht exemplarisch für diese Haltung. Es handelt sich um die umfassende Renovierung eines älteren Gebäudes, das zwar funktional und technisch stark überholt war, dessen architektonischer Charakter jedoch nach wie vor eine klare Qualität besaß. Die Aufgabe bestand nicht darin, etwas völlig Neues zu schaffen, sondern das Vorhandene weiterzudenken.
Der folgende Artikel dokumentiert diesen Prozess aus der Perspektive der Planung, der technischen Umsetzung und der inhaltlichen Entscheidungen. Er versteht sich nicht als theoretische Abhandlung, sondern als praxisnaher Erfahrungsbericht aus einem realisierten Renovierungsprojekt.
Das Gebäude und sein Kontext
Das Gebäude befand sich in einem gewachsenen urbanen Umfeld und war Teil eines etablierten Stadtgefüges. Seine Entstehung liegt mehrere Jahrzehnte zurück, was sich sowohl in der Bauweise als auch in der Grundrissstruktur deutlich zeigte. Zum Zeitpunkt der Renovierung entsprach es weder aktuellen technischen Standards noch zeitgemäßen Nutzungsanforderungen.
Gleichzeitig verfügte das Gebäude über Eigenschaften, die im heutigen Bauen selten geworden sind. Die Proportionen waren ausgewogen, die Fassadengliederung ruhig und präzise, und die verwendeten Materialien vermittelten eine handwerkliche Qualität, die über reine Zweckmäßigkeit hinausging.
Gerade diese Merkmale führten früh zu der Entscheidung, auf einen Abriss zu verzichten. Eine Renovierung erschien nicht nur wirtschaftlich sinnvoll, sondern auch architektonisch und städtebaulich verantwortungsvoll. Das Gebäude hatte eine Geschichte – und diese sollte nicht ausgelöscht, sondern weitergeführt werden.

Zielsetzung der Renovierung
Die Definition klarer Ziele war ein entscheidender Schritt zu Beginn des Projekts. Ohne eine präzise Zielsetzung besteht bei Renovierungen die Gefahr, sich in Einzelmaßnahmen zu verlieren oder widersprüchliche Entscheidungen zu treffen.
Im Zentrum stand der Anspruch, die architektonische Identität des Gebäudes zu bewahren und gleichzeitig seine Nutzbarkeit grundlegend zu verbessern. Die Renovierung sollte nicht museal wirken, sondern ein Gebäude hervorbringen, das heutigen Anforderungen gerecht wird, ohne seine Herkunft zu verleugnen.
Ein weiterer Schwerpunkt lag auf der strukturellen Sicherheit und der technischen Erneuerung. Das Gebäude musste den aktuellen Normen entsprechen, ohne dass diese Anpassungen sichtbar dominierend werden. Renovierung bedeutete hier, technische Notwendigkeit und gestalterische Zurückhaltung in Einklang zu bringen.
Bestandsanalyse als Grundlage jeder Entscheidung
Eine sorgfältige Bestandsanalyse ist bei jeder Renovierung unverzichtbar. In diesem Projekt bildete sie die Grundlage aller weiteren Schritte. Es ging nicht nur darum, Schäden zu identifizieren, sondern das Gebäude als System zu verstehen.
Die Tragstruktur wurde detailliert untersucht, ebenso die vorhandenen Materialien und deren Zustand. Dabei zeigte sich, dass viele Bauteile trotz ihres Alters noch über eine solide Substanz verfügten, während andere Bereiche gezielte Eingriffe erforderten.
Parallel dazu wurden die bestehenden Installationen analysiert. Heizung, Elektrik und Leitungsführung entsprachen nicht mehr den heutigen Anforderungen und mussten vollständig neu gedacht werden. Diese Erkenntnisse flossen direkt in das Planungskonzept ein und verhinderten spätere improvisierte Lösungen.
Entwurf und konzeptioneller Ansatz der Renovierung
Der Entwurfsprozess war geprägt von der Frage, wie viel Veränderung notwendig und wie viel Zurückhaltung sinnvoll ist. Renovierung bedeutet immer auch, Entscheidungen über Eingriffe zu treffen – und bewusst auf andere zu verzichten.
Die äußere Erscheinung des Gebäudes blieb weitgehend erhalten. Veränderungen an der Fassade wurden auf ein Minimum reduziert und beschränkten sich auf technische Optimierungen und notwendige Instandsetzungen. Neue Elemente wurden so gestaltet, dass sie klar als zeitgenössische Ergänzungen erkennbar sind, ohne sich in den Vordergrund zu drängen.
Im Inneren hingegen war mehr Spielraum für Anpassungen vorhanden. Hier konnte die Renovierung genutzt werden, um räumliche Qualitäten neu zu definieren, ohne die Grundstruktur des Gebäudes zu zerstören. Dieser bewusste Unterschied zwischen äußerer Zurückhaltung und innerer Weiterentwicklung prägte den gesamten Entwurfsansatz.
Statische Ertüchtigung und Sicherheit
Ein zentraler Bestandteil der Renovierung war die statische Ertüchtigung des Gebäudes. Altersbedingte Schwächen, frühere Umbauten und veränderte Nutzungsanforderungen machten gezielte Maßnahmen erforderlich.
Diese Eingriffe wurden mit großer Sorgfalt geplant. Ziel war es, die Tragfähigkeit und Sicherheit deutlich zu erhöhen, ohne die architektonische Erscheinung zu verändern. Verstärkungen erfolgten dort, wo sie konstruktiv sinnvoll waren, und blieben nach Möglichkeit unsichtbar.
Die Renovierung zeigt hier exemplarisch, dass Sicherheit und Ästhetik keine Gegensätze sein müssen. Durch präzise Planung lassen sich selbst umfangreiche statische Maßnahmen so integrieren, dass sie das Gesamtbild nicht beeinträchtigen.
Technische Erneuerung als unsichtbare Qualität
Die vollständige Erneuerung der technischen Infrastruktur war einer der aufwendigsten Teile der Renovierung. Alte Systeme wurden entfernt und durch zeitgemäße Lösungen ersetzt, die sowohl effizient als auch langlebig sind.
Besonderes Augenmerk lag auf der Energieeffizienz. Durch verbesserte Dämmung, optimierte Heizsysteme und eine durchdachte Haustechnik konnte der Energieverbrauch deutlich reduziert werden. Diese Maßnahmen sind nach außen kaum sichtbar, tragen jedoch maßgeblich zur langfristigen Qualität des Gebäudes bei.
Gerade bei Renovierungen zeigt sich, dass technische Qualität oft im Verborgenen liegt. Ein gut renoviertes Gebäude erkennt man nicht an auffälligen Installationen, sondern an seiner ruhigen, selbstverständlichen Funktionalität.
Räumliche Neuorganisation und Wohnqualität
Ein weiterer Schwerpunkt der Renovierung lag auf der Verbesserung der inneren Raumstruktur. Die ursprünglichen Grundrisse waren stark fragmentiert und entsprachen nicht mehr den heutigen Anforderungen an Flexibilität und Offenheit.
Durch gezielte Eingriffe konnten Räume geöffnet, Sichtbeziehungen verbessert und natürliche Belichtung verstärkt werden. Gleichzeitig wurde darauf geachtet, die ursprüngliche Logik des Gebäudes nicht zu zerstören. Die Renovierung verstand sich hier als Weiterentwicklung, nicht als radikaler Umbau.
Besonders wertvoll war die Reaktivierung zuvor wenig genutzter Bereiche. Flächen, die früher kaum Aufenthaltsqualität boten, wurden in funktionale und gut belichtete Räume transformiert. Dadurch gewann das Gebäude nicht nur an Fläche, sondern vor allem an Nutzungsqualität.
Materialien und Detailentscheidungen
Die Auswahl der Materialien spielte eine entscheidende Rolle für den Charakter der Renovierung. Neue Materialien sollten den Bestand ergänzen, nicht imitieren. Gleichzeitig mussten sie langlebig und wartungsarm sein.
In vielen Bereichen wurde bewusst mit einfachen, robusten Materialien gearbeitet, deren Qualität sich erst im Gebrauch zeigt. Details wurden reduziert ausgeführt, um den Fokus auf Raumwirkung und Proportionen zu legen.
Diese Zurückhaltung ist typisch für hochwertige Renovierungsprojekte im mitteleuropäischen Raum, insbesondere in Österreich, wo Klarheit und Ehrlichkeit im Umgang mit Materialien als Qualitätsmerkmal gelten.

Herausforderungen im Renovierungsprozess
Kein Renovierungsprojekt verläuft ohne Herausforderungen. Auch hier traten im Laufe der Umsetzung unerwartete Situationen auf, die flexible Anpassungen erforderten.
Besonders anspruchsvoll war die Koordination zwischen bestehenden Bauteilen und neuen Eingriffen. Jede Entscheidung musste sorgfältig abgewogen werden, da Fehler im Bestand oft schwerer zu korrigieren sind als im Neubau.
Durch eine klare Projektstruktur, enge Abstimmung aller Beteiligten und realistische Zeitplanung konnten diese Herausforderungen jedoch bewältigt werden, ohne die Qualität des Ergebnisses zu gefährden.
Projektbeispiel: Renovierung eines Bestandsgebäudes in Teheran (Iran)
Ein konkretes Beispiel für die im Artikel beschriebene Herangehensweise an Renovierung ist ein Projekt, das wir in Teheran realisiert haben. Das Gebäude befand sich in einem innerstädtischen Quartier mit überwiegend älterer Bausubstanz und wies deutliche Spuren jahrzehntelanger Nutzung auf. Ziel der Renovierung war es nicht, das Gebäude grundlegend zu verändern, sondern seinen baulichen Zustand präzise zu analysieren, Schwachstellen zu identifizieren und auf dieser Basis eine nachhaltige Erneuerung umzusetzen.
Ein wesentlicher Bestandteil dieses Projekts war die detaillierte Bestandsaufnahme vor Ort. Die vorhandene Bausubstanz wurde systematisch geprüft, unter anderem hinsichtlich Materialzustand, Oberflächen, Feuchtigkeitseintrag und thermischem Verhalten der Außenwände. Diese Untersuchungen bildeten die Grundlage für alle weiteren Entscheidungen und ermöglichten es, Eingriffe gezielt und verhältnismäßig zu planen, anstatt pauschale Maßnahmen anzuwenden.
Im Rahmen der Renovierung lag ein besonderer Fokus auf der Gebäudehülle. Die Außenflächen zeigten altersbedingte Abnutzungen, die sowohl ästhetische als auch funktionale Auswirkungen hatten. Durch eine Kombination aus Instandsetzung, materialgerechter Behandlung und gezielten Verbesserungen konnte die Substanz gesichert und gleichzeitig die Lebensdauer des Gebäudes deutlich verlängert werden. Dabei wurde bewusst darauf geachtet, den Charakter des Bestands zu erhalten und keine gestalterischen Brüche zu erzeugen.
Auch dieses Projekt verdeutlicht, dass Renovierung unabhängig vom geografischen Kontext nach denselben professionellen Prinzipien erfolgen sollte: sorgfältige Analyse, Respekt vor dem Bestand und klare Zieldefinition. Die Erfahrungen aus Teheran zeigen, dass eine strukturierte und verantwortungsvolle Renovierung nicht nur die technische Qualität eines Gebäudes verbessert, sondern auch einen langfristigen Beitrag zur Werterhaltung und Nutzbarkeit leistet.
Nachhaltigkeit und langfristige Perspektive der Renovierung
Ein zunehmend wichtiger Aspekt zeitgenössischer Architektur ist die Frage der Nachhaltigkeit. In diesem Zusammenhang gewinnt die Renovierung bestehender Gebäude eine strategische Bedeutung, die weit über rein wirtschaftliche Überlegungen hinausgeht. Jedes Bestandsgebäude repräsentiert bereits gebundene Energie, Ressourcen und kulturellen Wert. Eine sorgfältig geplante Renovierung ermöglicht es, diese vorhandenen Potenziale weiter zu nutzen, anstatt sie durch Abriss und Neubau zu vernichten.
Im vorliegenden Projekt wurde Nachhaltigkeit nicht als isoliertes technisches Ziel verstanden, sondern als integraler Bestandteil des gesamten Planungsprozesses. Bereits in der frühen Konzeptphase wurde geprüft, welche Bauteile erhalten, repariert oder angepasst werden können. Diese Herangehensweise führte nicht nur zu einer Reduktion von Bauabfällen, sondern auch zu einer bewussteren Auseinandersetzung mit dem Wert des Bestands.
Ein weiterer zentraler Aspekt der nachhaltigen Renovierung ist die Lebenszyklusperspektive. Entscheidungen über Materialien, Konstruktionen und technische Systeme wurden nicht allein auf Basis der Investitionskosten getroffen, sondern im Hinblick auf Wartungsaufwand, Langlebigkeit und Anpassungsfähigkeit. Gerade bei Renovierungen zeigt sich, dass kurzfristige Einsparungen häufig langfristig höhere Kosten verursachen können.
Darüber hinaus spielt die soziale Nachhaltigkeit eine wichtige Rolle. Eine Renovierung verändert nicht nur ein Gebäude, sondern beeinflusst auch seine Nutzer und sein Umfeld. Durch die Verbesserung von Raumqualität, Tageslichtführung und funktionaler Klarheit konnte das Gebäude wieder zu einem attraktiven und identitätsstiftenden Ort werden. Dies stärkt nicht nur die Nutzung, sondern auch die emotionale Bindung der Nutzer an den Ort.
Im internationalen Kontext wird Renovierung zunehmend als Schlüsselstrategie für eine verantwortungsvolle Stadtentwicklung verstanden. Während Neubau häufig mit hohem Ressourcenverbrauch verbunden ist, bietet die Arbeit im Bestand die Möglichkeit, bestehende Strukturen intelligent weiterzuentwickeln. Das hier beschriebene Projekt reiht sich in diese Haltung ein und zeigt exemplarisch, wie architektonische Qualität und ökologische Verantwortung miteinander verbunden werden können.
Nicht zuletzt hat dieses Projekt auch gezeigt, dass Renovierung ein Lernprozess ist – für Planer, Bauherren und alle Beteiligten. Der Umgang mit dem Bestand erfordert ein anderes Denken als der Neubau: weniger Kontrolle, mehr Dialog mit dem Vorgefundenen. Gerade in dieser Auseinandersetzung liegt jedoch ein großes kreatives Potenzial.
Zusammenfassend lässt sich sagen, dass Renovierung in diesem Projekt nicht als Einschränkung, sondern als Chance verstanden wurde. Als Chance, vorhandene Qualitäten sichtbar zu machen, neue Nutzungen zu ermöglichen und einen verantwortungsvollen Beitrag zur gebauten Umwelt zu leisten.

Fazit: Renovierung als nachhaltige Strategie
Die Renovierung dieses Gebäudes zeigt, dass Bestandserneuerung weit mehr sein kann als eine technische Notwendigkeit. Sie ist eine nachhaltige Strategie zur Stadtentwicklung, zur Ressourcenschonung und zum Erhalt kultureller Identität.
Dieses Projekt verdeutlicht, dass Renovierung dann besonders erfolgreich ist, wenn sie mit Respekt vor dem Bestehenden, klaren Zielen und einem langfristigen Qualitätsanspruch durchgeführt wird. Gerade im österreichischen Kontext, in dem historische Bausubstanz einen hohen Stellenwert besitzt, ist diese Herangehensweise von besonderer Bedeutung.
Renovierung ist in diesem Sinne kein Kompromiss, sondern eine bewusste Entscheidung für Qualität, Verantwortung und Kontinuität.
Ausblick
Die in diesem Artikel beschriebene Renovierung zeigt exemplarisch, welches Potenzial in der bewussten Arbeit mit dem Bestand liegt. In einer Zeit, in der Ressourcenknappheit, Klimaziele und städtebauliche Verdichtung zunehmend an Bedeutung gewinnen, wird Renovierung zu einer zentralen architektonischen Aufgabe. Zukünftige Projekte werden noch stärker darauf angewiesen sein, bestehende Strukturen intelligent weiterzuentwickeln, anstatt sie zu ersetzen. Die hier gewonnenen Erfahrungen bestätigen, dass eine präzise Analyse, eine klare konzeptionelle Haltung und interdisziplinäre Zusammenarbeit die entscheidenden Voraussetzungen für qualitätsvolle und nachhaltige Renovierung sind.
Referenz
1) EU-Gebäuderichtlinie – Energy Performance of Buildings Directive (EPBD)
Aktuelle EU-Richtlinie zur Gesamtenergieeffizienz von Gebäuden mit Renovierungszielen, Mindeststandards und nationalen Renovierungsplänen. Enthält Vorgaben zur Energieeffizienz bei Renovierungen.
https://en.wikipedia.org/wiki/Energy_Performance_of_Buildings_Directive_2024
2) National Building Renovation Plans – EU Kommission
Offizielle Seite der EU-Kommission zu nationalen Sanierungsplänen. Verpflichtet Mitgliedstaaten zur langfristigen Strategie für Renovierung und Dekarbonisierung des Gebäudebestands bis 2050.
https://energy.ec.europa.eu/topics/energy-efficiency/energy-performance-buildings/national-building-renovation-plans_en
3) Energieeinsparverordnung (EnEV) / Gebäudeenergiegesetz (GEG) – Germany
Regelwerk zu Mindestenergieanforderungen bei Neubau und Renovierung in Deutschland; EnEV durch GEG ersetzt, gilt für Energieeffizienz im Gebäudebereich.
https://en.wikipedia.org/wiki/Energieeinsparverordnung
4) OIB-Mindeststandards Energieeffizienz & Renovierungspässe – Österreich
Österreichische Informationsseite zu Mindeststandards der Gebäudeenergieeffizienz, Renovierungspässen und strategischen Renovierungsplänen gemäß EU-Gebäuderichtlinie.
https://www.oib.or.at/nicht-kategorisiert/mindeststandards-fuer-die-energieeffizienz-renovierungspaesse-und-nationaler-gebaeuderenovierungsplan-in-der-neuen-eu-gebaeuderichtlinie-folge-1-von-2
5) EU-Richtlinie zur Gesamtenergieeffizienz von Gebäuden – Energieverbraucher.de
Erklärung zur Energieeffizienzrichtlinie und zu Anforderungen bei größeren Renovierungen (Mindestenergieeffizienz bei Bestandserneuerung).
https://www.energieverbraucher.de/de/gebaeuderichtlinie__415/
6) Gebäuderichtlinie (EPBD) – Gebaeudeforum.de
Übersicht zu den zentralen Vorgaben der EU-Gebäuderichtlinie, darunter Renovierungspässe, Effizienzanforderungen sowie technische Normen (z. B. Energieausweis, Gebäudeautomation).
https://www.gebaeudeforum.de/ordnungsrecht/eu-vorgaben/epbd/
7) European Green Deal – EU-Klimaschutzprogramm
Überblick über die EU-Strategie zur Dekarbonisierung, inklusive ambitionierter Ziele für Renovierung und Energieeffizienz des Gebäudebestands.
https://en.wikipedia.org/wiki/European_Green_Deal
8) German National Action Plan on Energy Efficiency (NAPE)
Nationaler Aktionsplan Deutschlands zur Energieeffizienz, der auch energieeffiziente Renovierung im Gebäudesektor adressiert; Basis u. a. EU-Energy-Efficiency-Directive.
https://en.wikipedia.org/wiki/German_National_Action_Plan_on_Energy_Efficiency
9) Passive House / EnerPHit Standard (Weltweit anerkannt)
Standard für hohe Energieeffizienz im Neubau und bei Renovierungen (EnerPHit = Passivhaus-Konzept für Bestandsgebäude), relevant für energieeffiziente Renovierungspraxis.
https://en.wikipedia.org/wiki/Passive_house
10) Wikipedia – Energieeffizienzrichtlinie (EED)
EU-Richtlinie zur Energieeffizienz (EED), Teil des gesetzlichen Rahmens, der Renovierungsanstrengungen im Gebäudesektor unterstützt.
https://en.wikipedia.org/wiki/EU_Energy_Efficiency_Directive_2012